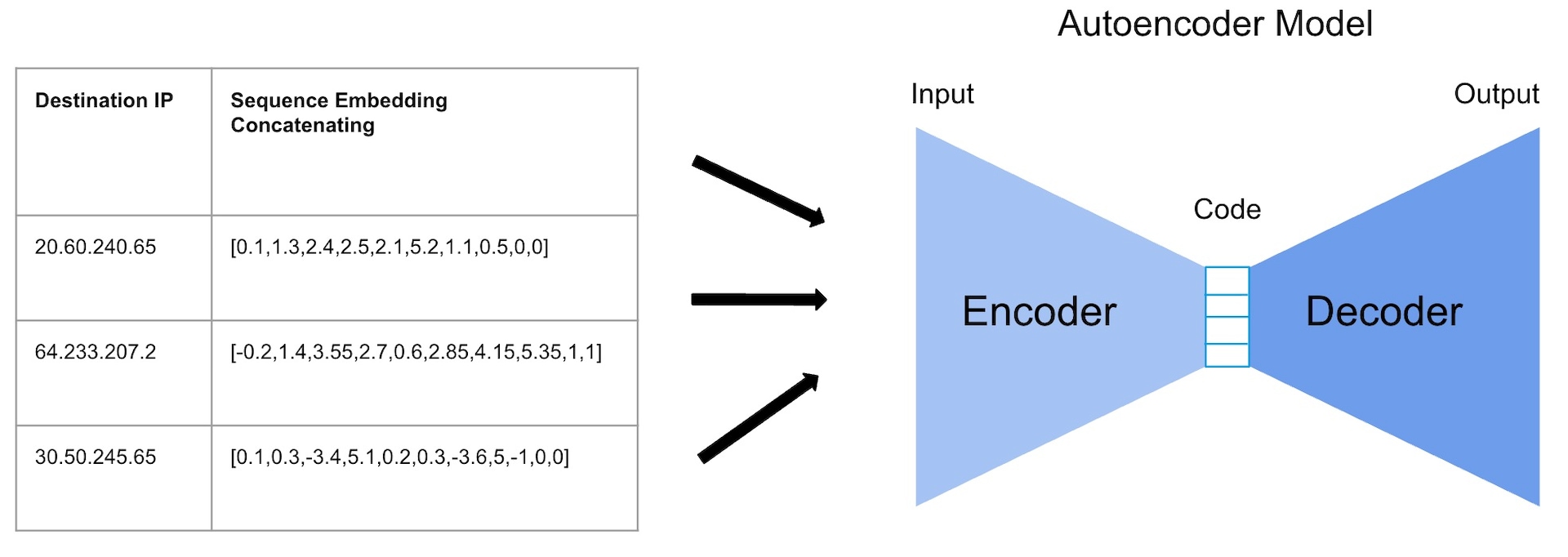
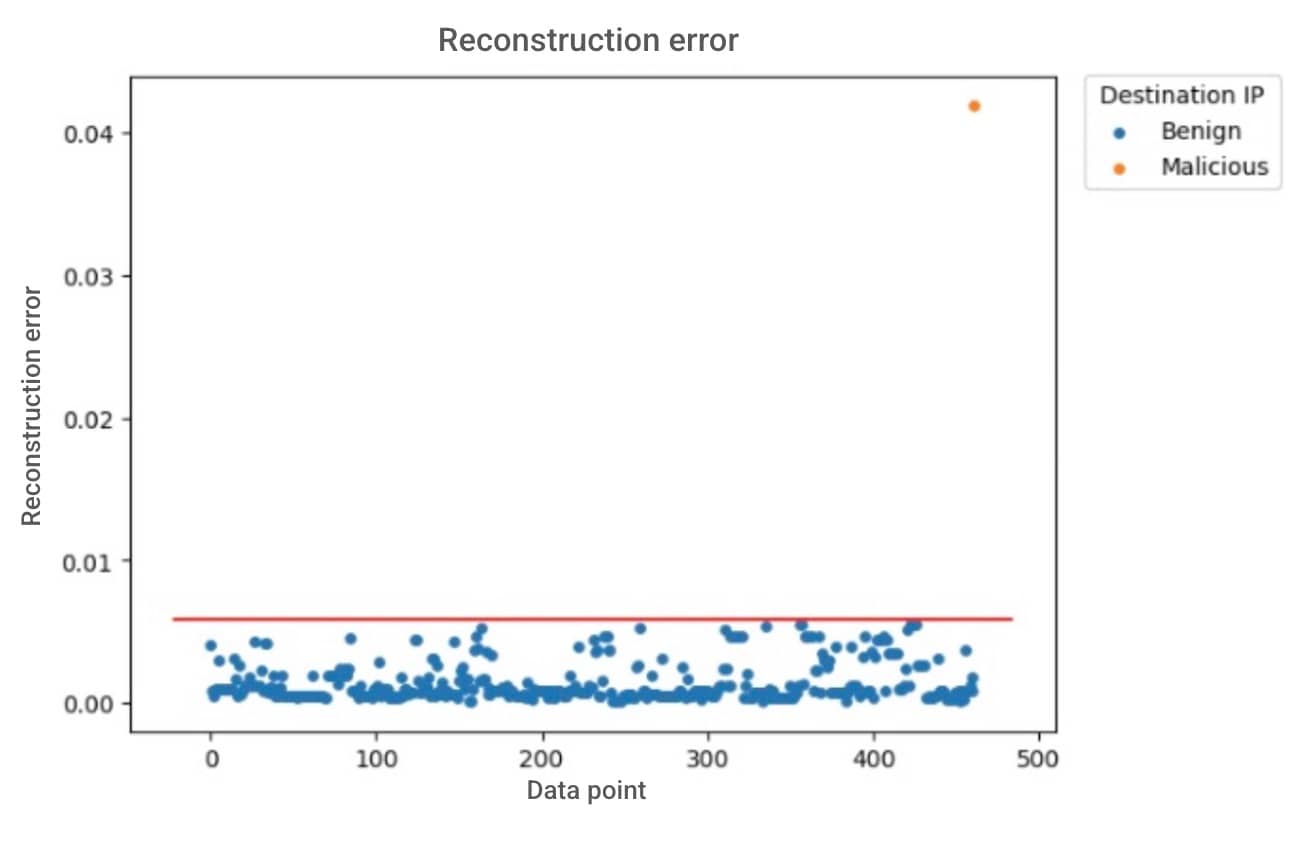
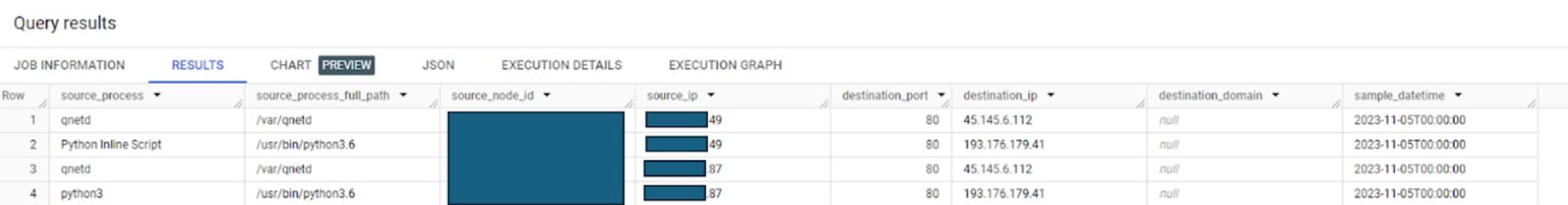
In 2012, IBM estimated that 90% of the world’s data had been created in the previous two years. Since then, data has become the fastest growing and most important asset for any organization. Every day, businesses are inundated with more data, higher consumer expectations, and the increasing pressure to make decisions at speed.
Welcome to the era of data observability
For organizations to stand out and truly deliver value, they must see and understand what’s happening across their data landscape, not just guess and hope for the best. That’s where data observability steps up and enables you to drive business change and innovation.
What is data observability?
Data observability isn't just a buzzword; it's a vital set of tools and practices that empower organizations to proactively monitor the health and flow of their data throughout the entire journey from ingestion to consumption. Instead of simply reacting to data issues after they arise, observability enables you to spot potential obstacles before they cause problems.
Seeing your data clearly can transform your business
Platforms like Akamai’s TrafficPeak offer real-time, granular visibility into traffic patterns, data streams, and performance metrics, essentially shining a spotlight into every corner of your data pipelines.
This deep insight helps you quickly identify bottlenecks, spot anomalies, and find inconsistencies long before they escalate into business-critical issues. Ultimately, data observability doesn't just protect your data quality; it fosters trust and confidence, unleashing the true power of data-driven decision-making.
The need for speed and smarts
The modern world runs on speed. Consumers expect instant gratification and personalized experiences 24/7. To meet these demands, business teams need real-time insights that allow them to pivot, adapt, and innovate without delay.
During peak periods, every second counts — and any downtime represents a lost opportunity that can’t be recovered. This fundamental shift means data is no longer secondary; it's the primary engine that’s powering every competitive advantage.
But a growing volume of data also brings a critical question: How can you truly trust what you're seeing? The smart answer is data observability.
When combined with powerful platforms like TrafficPeak, it delivers the confidence necessary to ensure your data is accurate, your insights are reliable, and your business is poised to operate at the velocity your customers expect.
How data observability gives you the edge
Adopting data observability isn't just a smart move; it's absolutely essential for any modern business. It begins with robust data quality assurance, which ensures that you're never flying blind by allowing you to spot errors, duplicates, and outdated information before any of it can lead you astray, thus fostering trustworthy data for consistently better decisions.
Enable faster problem-solving
When issues inevitably arise, data observability enables faster problem-solving by empowering your teams to quickly see and respond. Tools like TrafficPeak quickly pinpoint the root cause, minimize downtime, and keep your business running smoothly.
Facilitate proactive data management
Furthermore, data observability facilitates proactive data management, letting you anticipate changes, optimize performance, and scale confidently as your business grows. TrafficPeak's insights enable seamless resource allocation.
Deliver more value to consumers
Ultimately, by ensuring data you can truly trust, you're empowered to deliver more value to consumers by innovating to provide faster, better, and more personalized experiences that foster lasting customer loyalty.
The observable future: See clearly, lead boldly
Success in today’s business world demands more than just keeping up — it requires setting the pace. With robust data observability, powered by technologies like TrafficPeak, your organization gains the agility to react faster, seize new opportunities, and consistently deliver greater value to customers.
Data-driven capabilities have evolved — and observability is the force behind this evolution by transforming your data into a transparent and trustworthy asset that builds an organization that’s ready for any challenge.
In the rush to meet escalating consumer expectations and outperform competitors, data observability isn't optional; it's absolutely essential.
Observability bridges the critical gap between aspirational decisions and the confident, data-backed choices you can make today. With powerful solutions like TrafficPeak, you gain the clarity to see clearly, lead boldly, and let your data confidently guide your way forward.
Ready to lead with confidence?
Don’t just keep pace — set it. Embrace the power of data observability with Akamai’s TrafficPeak and turn your data into a strategic advantage. Gain the clarity to act faster, the agility to adapt smarter, and the confidence to lead boldly in a data-driven world.
Start your journey toward real-time, reliable insights today.
Tags